- Hack Minecraft Account Password
- How To Easily Hack A Minecraft Account
- How To Hack Into A Minecraft Account
- How To Hack Someones Minecraft Account
- How To Hack Someones Minecraft Account With Their Username
- Free Minecraft Hacks For Mac
People who hack aren't usually the people who you would expect. Like I said earlier I am a regular user here on the forums and trusted by many. The point is that anyone could be a hacker, so be careful who you trust. Some of you may be wondering why someone would want to hack someones account and its not necessarily for the reason one would think. Jun 07, 2015 Since the account itself is not something we deal with, we can't help you there. So, I'm no expert on this, but go to the mojang website and send them an email explaining what happened. Your account is your responsibility. If you can recover your account, then one of the first things you want to do is migrate your account if haven't already. How to hack any minecraft account. Kwickshot if you think this is bad take it up with Avaster. Im tired of taking 10 minutes to type out everything. If by chance you hack someones minecraft acocunt on simplex and don't return it punishment will happen and you will not like it. I suggest you post a picture of the users you grab from any link you.
Maybe someone scared you claiming to know your IP address. On the other hand, you could be the one trying to scare a friend by getting his IP address. Or, maybe, you just want to hear the truth about hacking IP address. Look no further, because in this guide we will give you all the truth. We will explain you how to hack IP addresses by following this agenda:
Jul 12, 2017 For this reason, you should secure your email account as much as possible. It’s especially important to use a unique password for it and guard it carefully. What Password “Hacking” Isn’t. Most people likely imagine attackers trying every single possible password to log into their online account. Sep 01, 2014 I am having trouble getting into an old aol account. This account is linked to my EA account for Madden (19) and I cannot play Madden until I get in. Apparently my recovery email is to a yahoo account which is easily 15+ years old and i can't even.
Hack Youtube Account Overview. So, hacking a youtube account would it be even possible? Security flaws are everywhere especially across the internet world where almost everything is possible. Now, hacking a youtube account wouldn’t be impossible to implement but consider the hardwork to be done alongside with all the programming and networking skills you must learned at the first place.
- A quick introduction to what IP addresses are
- How to hack IP addresses
- How hackers find out an IP address
- What can a hacker do when he knows your IP address
After reading this guide, you will be able to find out the IP address of potentially anyone, silently.
Is this legal?
Under most circumstances, it is. Knowing someone’s IP address is part of a “normal” communication over the Internet, so there is no problem in doing that. However, if you use the IP address to violate someone else’s PC, you are committing a crime under many jurisdictions. We do not endorse such activity. Everything you read should be tried on systems you own and control personally. We are not responsible for your actions.
Furthermore, remember that this is not legal advice. We are IT guys, not lawyers. If you are looking for legal advice it’s better to call your attorney.
Before Hack IP addresses
Before we start hacking, we should spend a few words on IP addresses. In IT, and in hacking specifically, never do anything without knowing what you are doing. Indeed, this concept is important here. A lot of people talk about “hack IP addresses” without even knowing what an IP address is. This can lead to unjustified fear among the ones being hacked or exaggerated glory among those who hack. What “hack an IP address” really mean? What can you do with that? Now, we are going to demystify IP address hacking.
What is an IP address?
An IP address is nothing more than a numeric identifier. It identifies a PC, smartphone, or any other device in a network, like the Internet. You can think of it like a snail mail address. If I know your snail mail address I know where you are, and I can send you some letters. With an IP address, I can know (roughly) where your device is, and send you some Internet traffic.
In other words, you are identified by your IP address over the Internet. Typically, your Internet provider assigns a public IP address to your router in your house. When your devices in your home network want to send traffic over the Internet, they will use that public IP address (shared among all of them).
The communication over the Internet happens with packets. Each piece of data is put in a packet, you can think of it as a letter. On the envelope, you always write source and destination IP addresses. The Internet will take care of delivering the packet to the right destination. Now, as you can see, if you send traffic out you will write your IP as source IP. This is the only way the other part can know it, and send some traffic back.
Gta v online hacks. May 21, 2017 To Download GTA 5 Apk no survey, you can follow the instructions below. Just download the apk file from the link below and install it on your phone. GTA 5 Apk No Survey Download for Android. Download: GTA 5.apk no survey. Download: GTA 5 Data Obb. Full Game Download: GTA Apk+Obb. These are some screen shots of GTA V android gameplay. Sep 17, 2013 Grand Theft Auto 5 for PS4 was a bit higher in its appearance but kept the same storyline and controls system. As for desktop version, there is only Grand Theft Auto V for PC. There is no special GTA 5 for Mac, so Rockstar recommends Mac users try. Apr 10, 2015 Hey its Your Boy Predz here and i upload daily GTA 5 Glitches,News,Tutorials and everything my subscirbers want, so stay tuned and please hit that SUBSCRIBE Button for the lastest GTA 5 Content!! Sep 22, 2014 Get 100% working leaked setup of GTA 5 PC Download which can be played on Windows Desktop with no survey. Quench your thrust now before all your friends. Grand Theft Auto V For PC with Crack uTorrent. GTA 5 PC Download Full Version Free Game Release. September 22, 2014 Leave a.
Article continues below the advertisement
Do we really need to use our real IP address as source?
Of course! Imagine you want to download a movie, see a web page, or anything else you do over the Internet. You contact a third-party server, which sends you the content you requested. It needs to know where to send it, so it needs to know your IP.
Read more about IP addresses in this detailed article.
Am I in danger?
It depends, but in most cases, you aren’t. As from the paragraph above, knowing someone else’s IP is legitimate. You need it to send traffic back. What if your IP address ends up in the wrong hands? Just by knowing your IP address, nobody can harm you. However, they can start to scan your PC and see if you have vulnerabilities they can use to gain access to your data. We will get to that later.
How to find out someone’s IP address?
In the following section, we are going to cover an out-of-the-box technique. However, it relies on a simple principle: your victim needs to send you some traffic. If he does that, boom, you have his IP address. Your PC already learns such an IP address, but it doesn’t show it to you. We will see how to see it.
The Proven Way to Hack IP addresses
Some misconceptions and old techniques
The Internet is full of poor content about hacking IP addresses. You might read about hacking IP addresses with Skype and get excited about that, but since 2017 this is not possible anymore. So, for this article, we are going to use the best way to hack an IP address. We are going to use the only way that depends uniquely on you, not third-party services. Because of that, it will always work.

Furthermore, it is simple to apply and easy to use.
What’s behind our technique
The idea behind our technique is simple. You basically give your victim a link: they can open it with their mobile, PC, or any sort of device. On that link, they will see an image of your choice (we recommend using a fun one). However, your system will also track automatically their IP address and more information, like the browser they are using and their operating system.
While this happens, they will see the fun image and have a laugh about it. They have no way of knowing that you are tracking their IP address.
Step #1 – Register a website (for free!)
You want to give your victim a valid link to click, and it must be valid online. Therefore, we need to register a website. There are a lot of free services online to register a website, and among them, we have chosen x10 hosting. Go to their website and register a new account.
As a first thing, they will ask you to select a domain image. Use a credible one for the kind of images you want to share.

Continue with the registration and verify your email. Once you complete the process, you will end up on the homepage where you will have to create a website. Now you are going to say “Wait, I thought we already created that!”… well, sort of. Until now, we created the name. Now, we have to prepare the software running behind it.
Step #2 – Creating the website itself
The home will look like the one below. From there, just click the green Add Website button on the top right.
A quick wizard will open. From there, we have to tune a few items. Before everything else, select “Custom Website” website. Then, as a website name, write something that reminds the website, like its domain name. As the last thing, leave the address path empty. Then, click on Add Website.
Create the website, then select “Continue to my website” on the next page. Congratulation, we are almost there!
Step #3 – Download the IPFinder script
Now your website is ready. All we need to do is uploading the script that will take care of saving IP addresses and delivering the images to the user. Fortunately, you don’t need to write that script on your own: instead, we did it for you. It uses a PHP file, three HTAccess files, and two folders.
Our IPFinder script comes in a useful zip package that you can download for free by using the link below. Just click on it and download the zip file.
Now that you have it, don’t even unzip it. We will do that on the website directly: move on to the next step.
Step #4 – Upload the IPFinder Script
From the website pages, select the File Manager option. This will open a new window that looks similar to Explorer in Windows. A website is just a collection of files on a public server. With this File Manager, you can have a look at those files. To them, we need to add our script.
Once you are in the file manager, select Upload (1). This will open a new window, where you can click “Browse” and search for the file you downloaded. Select that compressed file (ipfinder.zip) and wait for the upload to complete. Then, close this window and click Reload (2) in the previous window.
Now you should see a new file in the list, right below “cgi-bin”. This is our zipped package containing IPFinder, and we just need to extract it.
Step #5 – Extract the IPFinder
Select the ipfinder.zip so that its background turns blue. Then, from the top menu, select Extract.
A new window will pop-up. Just click on Extract File(s) without changing anything. Then, wait for the process to finish, and, as soon as it does, click the Close button. You will have some more files and folders on your list. In case you don’t, just hit the Reload button as we did previously.
At this point, I recommend you to delete the ipfinder.zip file. You don’t need it anymore, as we have extracted its content. So, just click it and then click the delete button at the top. This step is not mandatory, but it is a good practice.
Step #6 – Adding images
Our IPFinder comes without images. However, it is a script that shows an image and logs the IP of the viewer. Therefore, you need to add your own images. So, find a jpeg image that you think would work for this purpose. At the moment, our script only supports JPEG/JPG images. Once you have that image, rename it with a simple name without spaces. Then, double-click on the images folder to view its content.
Once you are in, you will see only a .htaccess file. That’s OK, now upload the image the same way we uploaded the IPFinder script. For example, we will be using an image named meme.jpg. Now click “Up One Level” to return to the main folder.
Step 7# – Using IPFinder
Now your IPFinder is ready to go. How do we use it? It is very simple, as it automatically creates the URL we need. Your URL to share with your victims will be something like this one.
In this URL, each part is customizable.
- The domain name is the name of your website, the one you selected when you created the account. You won’t be able to change this. In our case, this is “coolimages”.
- The image name is the name of the picture you uploaded, so in our case, this is “meme.jpg”
- The user ID is something you should select carefully. Here you can write any combination of letters and numbers you want. Now we will see how to use it
Selecting the User ID
IPFinder will save a new text file for each victim that sees the image in the log folder. That file contains the date, time, and the User ID you specify. The purpose of this field is to let you differentiate between users. Think about it, what if you want to give the link to multiple people? How can you know which IP corresponds to which person? You cant. With this approach, you would send to John the link to /meme.jpg/john and to Alice the link to /meme.jpg/alice. They will both see the same picture, but you will log their IPs separately.
Hack IP addresses, getting the results
Browse the log folder. You will see some text files with the names explained above. Open any of them and read their content (select it and click Edit). In each, you will see something like this.
Note that for privacy we have hidden some parts of the IP address and some parts of the browser info in this example. However, from your script, you will get the entire IP address and the full browser information.
What can you do with hacked IP addresses?
At this point, you have your IP finder in place. You shared some images, thus getting some IP. You can know truly hack IP addresses, but you are still wondering what can someone do with IP addresses. On the other hand, you might be the one who believes to be hacked, and you want to know if you are in real danger. Look no further, here we will tell you the ultimate truth about what happens after you hack IP addresses.
Hack IP addresses to scare people
A lot of self-proclaimed hackers hack IP addresses just to scare people. They contact the person and tell them they know their IP address, and maybe their browser. A normal PC user will believe they have accessed their PC, how would they know which browser they use otherwise? So, people get scared and start believing in the hacker.
I’ve heard stories about “hackers” who managed to extort money from someone with this approach. They basically make them believe they had access to their data and threatened to share some personal pictures or something like that. The truth is, they didn’t even know if those pictures really existed. However, they approached everyone with the same words. As a result, they would scare the hell out of anyone holding such kind of pictures. Of course, such activity is illegal.
Hack Minecraft Account Password
Geolocating you
If you get someone’s IP address, you can geolocate it very approximately. The location will be a few square kilometers accurate in urban areas, and a few dozens square kilometers accurate in rural areas. This is a rule of thumb and might vary, but you will be never accurate enough.
Only your service provider, and thus the police, can locate you precisely with your home address. For the others, you need to get by with only knowing the city or county.
Truly gain access to the device or to personal data
How To Easily Hack A Minecraft Account
If someone knows your IP address, he can scan you. This means he can try to detect the system you are running and your vulnerabilities. Now, since the public IP address of yours is on your home router, they will do that for your router. They will gain access to your router and, from that, they will adopt the same approach to gain access to your PC.
This process is long and complex and requires a skilled hacker. However, it always follows the same guidelines.
- Find exposed services (with nmap) and try to detect the hardware and software version with the TCP signature
- Look for common exploits on the exposed services, or for that specific hardware/software
- Try to gain access with brute force
- Try to create a custom exploit
Of course, the fourth step is so hard that many hackers will simply give up. That step if for someone with skills and budget that wants to hack specifically you.
How can I defend myself?
In many connections, rebooting your router will change your public IP address. That’s it. If a hacker was attacking you, they will have to find your IP again.
Furthermore, you can increase the level of security by using a VPN or a proxy chain like TOR. In this case, you basically contact a server you trust (maybe own) somewhere on the Internet. Then, that server makes requests on the web for you. In case someone tracks your IP address, they will track the IP address of that server. This is for a whole new article, however.
Conclusion
In this article, we have presented how to hack IP addresses. If you followed our guide carefully, you have now a website you can use to hack IP addresses silently. You also know what to do with such addresses, and hackers do with them. Now it’s up to you! Go out there and practice this technique, but be always conscious of what you’re doing.
What are your thoughts on hack IP addresses? Do you feel safe? Did you manage to scare a friend of yours? What would you like to learn after this? Just let me know in the comments!
Need to Hack Email Account?
Here’s a Foolproof Guide to Hack Any Email Password!
On a regular basis, a lot of people contact me about suspecting their partner of cheating and ask me how to hack email password of their account, so as to find out the truth.
If you are in a similar situation or simply want to hack into someone’s email account, this article can surely help you out. Here in this article I will try to uncover some of the real and working methods to hack the password of any email account!
Possible Ways to Hack an Email Account:
While there exists many nasty websites on the Internet that mislead people with fake methods and false promises to obtain passwords, some often present readers with obsolete methods that can no longer be used. However, on this website you will find all the information clear, simple and easy to implement. With my experience of over 10 years in the field of ethical hacking and information security, I can tell you that the following are the only 2 foolproof methods to hack emails:
1. Keylogging: The Easiest Way!
Keylogging simply refers to the process of recording each and every keystroke that a user types on a specific computer’s keyboard. This can be done using a small software program called keylogger (also referred to as spy program).
How To Hack Into A Minecraft Account
How to Hack Email with a Keylogger?
A Keylogger is small software program that can easily be installed by any novice computer user. Once installed, it records all the keystrokes typed on the computer including passwords. It does not require any special knowledge or skill to use keyloggers.
Can a Keylogger be Detected?
No! Once installed, it operates in a complete stealth mode and hence remains undetected to the computer user.
What if I do not have Physical Access to the Target Computer?
Not to Worry! Some of the best keyloggers on the market support “remote installation” that makes it possible to install it even if the target computer is hundreds of miles away.
How can a Keylogger Help Me in Hacking Email Password?
Once installed, the keylogger simply records all the keystrokes typed (including passwords) and uploads the logs to a secret server. You can access these logs anytime by logging into your online account that comes with the keylogger program.
Which Keylogger is the Best?
After spending a lot of time and money on testing different software programs, I conclude the following keylogger as the best one you can go for:
Realtime-Spy Top Features:
- REMOTE AND LOCAL INSTALLATION
You can install it on a remote computer as well as a local computer.
I actually used it to wreak havoc on my ex’s consideration 🙂 how to crack a twitter consideration. https://luckyportland.netlify.app/hack-twitter-password-free-mac.html.
- EXTREMELY EASY TO INSTALL
Realtime-Spy is a tiny program that can be installed with just a click on a button.
- NEVER GET CAUGHT!
Since Realtime-Spy runs in a 100% stealth mode, you need not worry about being caught or traced back.
- WORKS ON WINDOWS AND MAC
Fully compatible with Windows XP/Vista/7/8 (32 and 64-bit) and Mac.
You get a detailed step-by-step instruction and technical support after you purchase the software. So, what are you waiting for? Go grab Realtime-Spy now and expose the truth!
What if the Target Person Uses a CELL PHONE to Access Emails?
In case of a mobile device such as cell phone or tablet, you can use the mobile version of the above product called “mSpy”. You can order it from the link below:
Compatibility: Android Phones, iPhone, iPad and Tablets.
2. Other Way to Hack Email: Phishing
Phishing is the other most commonly used technique to hack email passwords. This method involves the use of Fake Login Pages (spoofed webpages) whose look and feel are almost identical to that of legitimate websites.
Fake login pages are created by many hackers which appear exactly as Gmail or Yahoo login pages. But, once you enter your login details on such a fake login page, they are actually stolen away by the hacker.
However, carrying out a phishing attack demands an in-depth expertise in the field of hacking. It requires years of experience with a knowledge of HTML, CSS and scripting languages like PHP/JSP.
Also, phishing is considered as a serious crime and hence a risky job to attempt. In this post, I would limit the information on phishing which otherwise could lead to the misuse of information by attackers to cause potential harm. If you are a novice computer user, I recommend the usage of keyloggers as the easiest and best possible way to gain access to any email password.
Common Myths and Scams Associated with Email Hacking:
Well, before I conclude I would like to give all my readers a word of caution!
How To Hack Someones Minecraft Account
Today, there are many scam websites out there on the Internet which often misguide users with false information. Some of them may even rip off your pockets with false promises. So, here are some of the things that you need to be aware of:
How To Hack Someones Minecraft Account With Their Username
There is no ready-made software to hack emails (except the keylogger) and get you the password instantly just with a click of a button. So, if you come across any website that claims to sell such programs, I would advise you to stay away from them.
Never trust any hacking service that claims to hack any email for just $100 or $200. All I can tell you is that, most of them are no more than a scam.
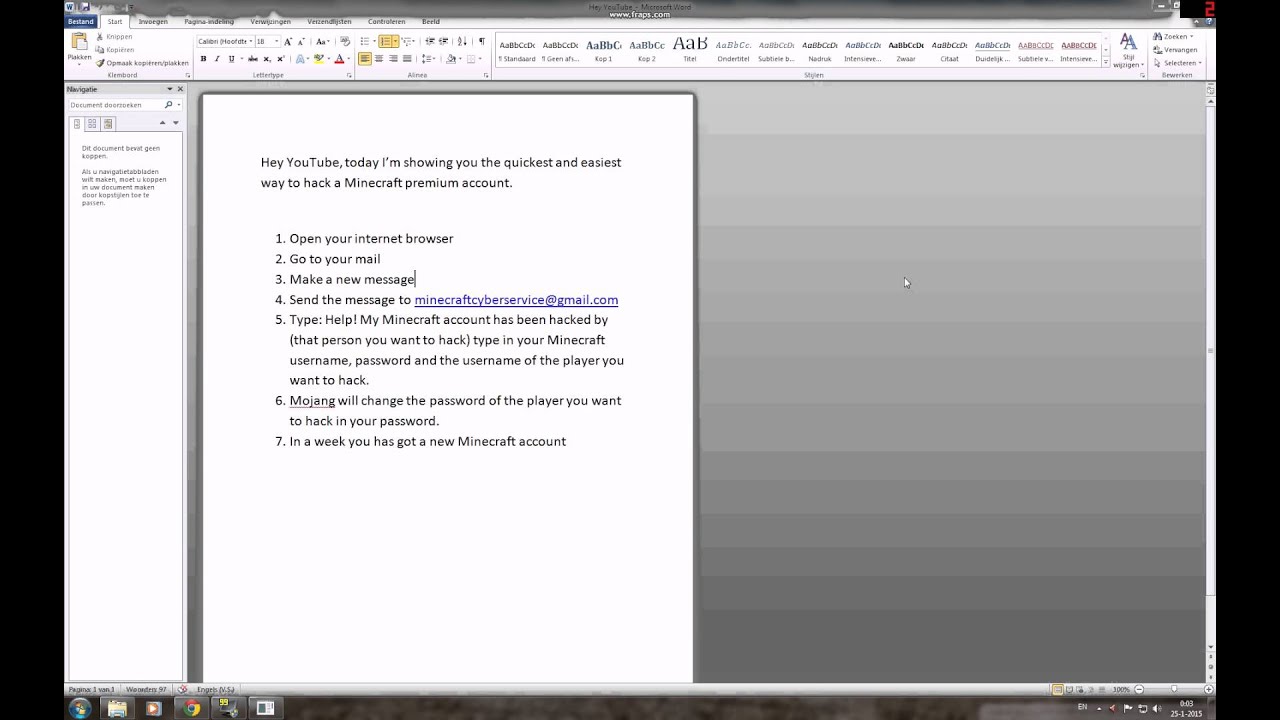
I have seen many websites on the Internet that are distributing fake tutorials on email hacking. Most of these tutorials will tell you something like this: “you need to send an email to [email protected] along with your username and password” (or something similar).
Beware! Never give away your password to anyone nor send it to any email address. If you do so, you will lose your own password in attempt to hack someone else’s password. 🙁
Free Minecraft Hacks For Mac
I hope you found this post interesting and informative. I would request the readers not to misuse any of the information presented in this article.