Howdy guys welcome to RapidTopic today I will discuss some DDOS Attack Tools. You might be wondering what is DDOS. The full form of DDOS is Distributed Denial of Service attack it is hacking technique people used for hacking online websites and applications. DDOS Attack Tool is made for penetration testing for any website But some people use it for hacking which is illegal.
Contents
Dec 12, 2016 Here are the top 5 hacking tools that are used by Hackers. These tools are available for Windows, Mac Os, and Linux. This is Teja! In this video, I will be showing the top 5 hacking tools. Dec 01, 2016 Best 5 Apps to Extract or Open RAR files on Mac OS X RAR files are commonly known as compressed files, although it’s used for archiving files in a single package as well. A lot of third party programs are available for different operating systems to open and extract RAR files, among them WinRAR is apparently the most popular. Jul 24, 2018 Howdy guys welcome to RapidTopic today I will discuss some DDOS Attack Tools.You might be wondering what is DDOS. The full form of DDOS is Distributed Denial of Service attack it is hacking technique people used for hacking online websites and applications.DDOS Attack Tool is made for penetration testing for any website But some people use it for hacking which is illegal.
- 0.1 What Is a DDOS Attack?
- 1 Best DOS/DDOS Attack Tools
What Is a DDOS Attack?
DOS/DDOS Attack is an attempt to make an online service unavailable by overwhelming it with traffic from different resources. In research by Arbor, networks found that more than 2000 malware DDOS attacks are being observed daily.
So How They send huge traffic in DDOS Attack to their target.
Well, Attackers build their network of millions of computers they send the malware to thousands of computer by Emails, social media, and websites. They can remotely control these computers anytime for using them to send traffic to their target website.
So today we will discuss some DDOS Attack Tools which used for testing a website.
Note- Our website Does not support hacking or any illegal activities this Article is only for Educational Purpose. We are not responsible for any illegal activity.
Best DOS/DDOS Attack Tools
Low Orbit Ion Cannon (LOIC):
Low Orbit Ion Cannon is an open source network stress testing and DOS attack software. It is written in C#. The developer behind this tool is praetox Technologies. It will work by providing the huge TCP and UDP packets on the target with the intention of disrupting its services. It is available on Linux, Windows, and Android.
SlowLoris:
It is one of the best DDOS attack tools invented by Robert Hansen “R Snake”. It works by connecting to the target web server by the thousands of connections and opening and holding the connection as long as possible. Slowloris sends a partial HTTP request to the web server And it will result in filling the maximum number of connections and denying in the Real visitor’s connections.
It requires minimal bandwidth to target web server and it has no side effects. It is available on GitHub.
HOIC (High Orbit Ion Canon)
HOIC is designed to replace LOIC(Low orbit ion connection) by praetox technologies. It is written in BASIC it can attack 256Urls simultaneously.
It performs a DDOS attack by sending the huge traffic to the target website at the same time. HOIC sends the HTTP POST and GET requests to a target computer.
It is available on Linux, Windows, and Mac.
RUDY (R_U_DEAD_YET)
Rudy is a very slow DDOS attack tool which is made for crashing web server by submitting long form fields. R.U.D.Y tool automatically detects the web forms of the target web server and send numerous of small packets at a slow rate which ultimately crashes the server of the website by filling the connection table.
Golden EYE
GoldenEye is a very popular tool used for network stress testing of a web server. It is written in python. You can find it on GitHub it is mentioned that it is for security testing purpose only.
XOIC
XOIC is another DDOS attacking tool. It is the simplest among all the tool a beginner can use this tool easily. XOIC performs an attack by an IP address and a user-generated port and a user selected port.
It has three attacking mods. The first mode is a TEST which is used for testing. The second and third are used for Basic DDOS attack and DDOS attack with a TCP/HTTP.
Pyloris
Pyloris is a scriptable tool for a testing vulnerability in the server to connection exhaustion denial of service attacks. it can utilize socks proxies and SSL connections, and it can target protocols such as HTTP, FTP, SMTP, IMTP, and Telnet.
It is available on Windows, MAC, and LINUX.
TOR’s Hammer
Tor’s hammer is our eight best DDOS tool. It is written in python and available on Linux. It is a slow post-DOS testing tool. You can run it with TOR it assumes you are running it with TOR on 127.0.0.1:9050. It can kill most unprotected web servers running Apache and IIS via a single instance.
HULK:
HULK is a Denial of service attack tool that is meant to put a heavy load on servers in order to bring them to their knees by exhausting the resource pool, you can get it from Git Hub.
10. THC-SSL-DOS:
This tool is developed by the Hacker’s choice. This tool will check the vulnerability in the SSL and crash a server. This does not need any bandwidth like a traditional DDOS tool it works from a single attack computer. You can download this software form THC official website.
The THC-SSL-DOS tool is a Proof Of Concept tool to disclose fishy security in SSL.
Wrapping Up:
So these are the top 10 DDOS Attack Tools if you are testing your website or any clients website of network penetration then you use one of these DOS Attacking tools and find the vulnerability to fix them. I hope you enjoyed this article share it on social media with your friends.
these softwares are for testing only. Doing DDOS attack is illegal
20 Free Hacking Software
The Internet is filled with unlimited number of Hacking software. We have also talked a lot about these hacking software on our past articles. Hence today we have decided to list the best Hacking tools that are free to download. We will also add the download link and tutorials wherever necessary.
So let’s begin with our list of 20 best free Hacking Software. Note that these softwares are used for security and academic purpose. Most of them might be banned in your workplace. Hence use them at your own risk.
Note: We have divided our list into Wifi cracker, Password cracker, Port scanners and Intrusion detection tools.
Free Hacking Software to Download
Password Crackers:
1: THC Hydra:
THC Hydra is a tool for brute force attack from remote login. It is used to perform a dictionary attack on around 50 protocols such as telnet, ftp, http, https, smb, etc. THC Hydra can be paired with Kali Linux or Aircrack-ng for better results.
2: Brutus:
Brutus is the most popular and preferred Password hacking software. It is same as THC Hydra and is used to perform a remote hack. Brutus is also available for Windows Operating system.
3: Medusa Password Cracker:
Medusa is one of the fastest password cracker that uses brute force attack. It can support HTTP, FTP, CVS, AFP, IMAP, MS SQL, MYSQL, NCP, NNTP, POP3, PostgreSQL, pcAnywhere, rlogin, SMB, rsh, SMTP, SNMP, SSH, SVN, VNC, VmAuthd and Telnet.
4: Ophcrack:
Ophcrack is a well known hacking software. It is based on Rainbow tables. Ophcrack is easily available for Windows and Linux platforms.
5: Fgdump:
One of the popular feature of Fgdump is that it can even run with Antivirus. It is usually used to retrieve passwords from cache files of the target user.
WiFi Hacking Software:
6: Pyrit:
Pyrit is a WiFi hacking tool used to crack WEP WLAN passwords. Below is a indepth YouTube tutorial about Pyrit.
7: CloudCracker:
Cloudcracker is a password cracking tool which generates passwords using hash files. You need to upload Hash files created by a hash file generator tool like Hashcat. Cloudcracker is an online tool which can be accessed via their official website here.
8: Fern WiFi Cracker:
Fern is especially designed for Windows, Apple and Linux users. It was developed for testing network penetration and vulnerability. But now it is used as a major WiFi hacking software.
Fern is used to detect major flaws and vulnerabilities on a Wireless network. You can then exploit those flaws to gain access to a network.
9: Cowpatty:
Cowpatty is a well known name in hacking community. It is an inbuilt tool of Kali Linux and is used for advanced hacking. Cowpatty is compatible with both Linux and Windows environment.
Download Cowpatty WiFi hacking Software
10: Kismet:
Kismet is used to crack Wi-Fi 802.11 a/b/g/n layer2 networks. It is basically a network sniffer and captures packets to determine username and passwords. Kismet is also used to identify hidden networks. You can get Kismet hacking tutorials from their official website.
11: Commview:
Commview is a certified Wireless analysis tool. It is used by professional experts to monitor wireless networks. Its wireless analysis tool is too powerful and can be used as a tool to exploit networks.
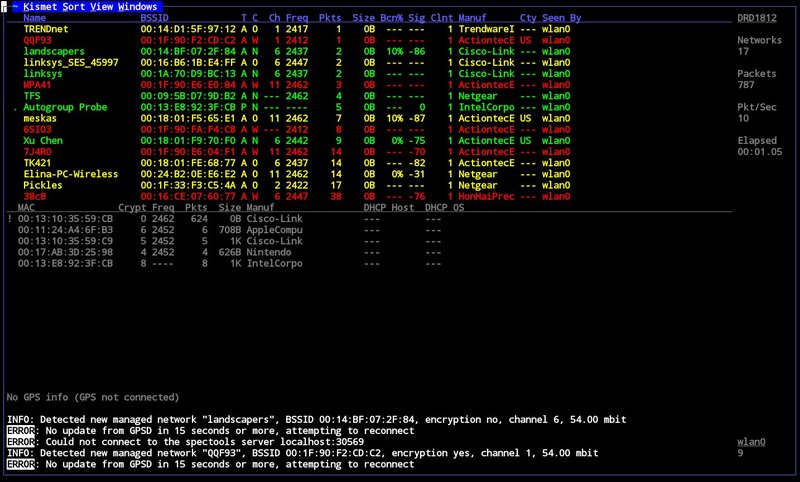
12: Omnipeek:
Omnipeek is used to capture and analyze data packets. It is same as Wireshark, but is better in capturing packets. With Omnipeek you can even look into browsing history and Login Used Id’s and passwords.
Download Omnipeek WiFi hacking Software
13: WEPattack:
As the name suggests, Wepattack is used to hack WEP/WLAN networks. This software is best for hacking old modems and routers. You can also use Wepattack to monitor and analyze data traffic.
14: Netstumbler:
Netstumbler is used as an exploitation tool to generate major flaws on a wireless network. Once a weak link is identified, it exploits the network and crack it. Netstumbler is available for both Windows and Linux systems.
15: Aircrack:
Aircrack is one of the most used WiFi cracking software used for 802.11a/b/g WEP and WPA cracking. It attacks a network by using the FMS attack and recovers data packets. These packets are then gathered and analyzed to recover the WiFI password.
Port Scanners and Encryption tools:
16: Angry IP Scanner:
It is an open source IP scanner used to scan IP’s connected to a network. It then detects harmful connections. You can also share files using remote desktop connection.
Download Angry IP Scanner Intrusion Detection Tool for Free
17: NetCop:
NetCop works as a firewall and antivirus and protect your network from illegal packets. This tool is best for users who have highly confidential data and want it to secure from network hackers. It comes with features such as ClamAV Antivirus, Web Cache, Content Filter,IPS/IDS, WAN Link Manager, Bandwidth Manager, Anonymous Proxy Blocker, Wifi Hotspot Controller, SSL VPN, Network Virtualization.
18:Putty Encryption tool:
Putty is an open source tool developed for Windows encryption and security. It is used to create a secure Remote connection and is used to encrypt SSH, Telnet, and RLogin protocols.

19: OpenSSH:
OpenSSH is used to encrypt network connections from eavesdropping, connection hijacking, and other attacks. This tool also provides remote login with SSH protocol. OpenSSH is generally used when you have to send data via the Internet from one source to another.
Best Hack Tools For Amazon Kindle Fire
20: TrueCrypt:
Best Hacking Tools For Macos
TrueCrypt is used to secure your system files and folders from outside threats. It can encrypt any file, folder, drive or partition. TrueCrypt is now discontinued for support, but can still be downloaded.